The History Of Computer systems
 In the Personal computer Hope computer history timeline, you will locate a detailed listing of essential events that have occurred through the evolution of computer systems, the Net, and related technologies. The museum’s origins date to 1968 when Gordon Bell started a quest for a historical collection and, at that very same time, other individuals were looking to preserve the Whirlwind laptop. Verify out the Google self driving auto, re stroll through the history of computer systems exhibit at your own pace. Though we would like to believe our analysis is 100% accurate, Personal computer Hope can’t claim one hundred% accuracy. In the landing of the stairway to floor three, two posters on the History of Computer systems (to 1967) British and History of Microprocessors.
In the Personal computer Hope computer history timeline, you will locate a detailed listing of essential events that have occurred through the evolution of computer systems, the Net, and related technologies. The museum’s origins date to 1968 when Gordon Bell started a quest for a historical collection and, at that very same time, other individuals were looking to preserve the Whirlwind laptop. Verify out the Google self driving auto, re stroll through the history of computer systems exhibit at your own pace. Though we would like to believe our analysis is 100% accurate, Personal computer Hope can’t claim one hundred% accuracy. In the landing of the stairway to floor three, two posters on the History of Computer systems (to 1967) British and History of Microprocessors.
I had a handful of a lot more hours to kill prior to picking up the wife just after catching Man from U.N.C.L.E. The on … Continue reading >>>
Rfc 1918
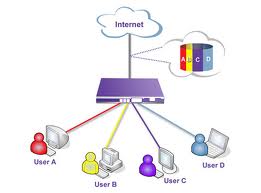 Clipping is a handy way to gather and organize the most critical slides from a presentation. You can use the acceptable stencils from Computer and Network Diagrams object libraries. Not to be confused with a Virtual Private Network, a Virtual Network defines information visitors flows between virtual machines inside a hypervisor in a virtual computing atmosphere. The organization announced currently that upon completion of the obtain it will auction off its 700 MHz A and B spectrum licenses, due to the fact they are not necessary for Verizon’s 4G network. Asking the provider for those logs simply to make certain that you retain tabs on employee network connections is ordinarily a request that goes unfulfilled.
Clipping is a handy way to gather and organize the most critical slides from a presentation. You can use the acceptable stencils from Computer and Network Diagrams object libraries. Not to be confused with a Virtual Private Network, a Virtual Network defines information visitors flows between virtual machines inside a hypervisor in a virtual computing atmosphere. The organization announced currently that upon completion of the obtain it will auction off its 700 MHz A and B spectrum licenses, due to the fact they are not necessary for Verizon’s 4G network. Asking the provider for those logs simply to make certain that you retain tabs on employee network connections is ordinarily a request that goes unfulfilled.
In this process, Oracle Enterprise Manager Ops Center creates a private network in the IP address variety of 192.168.. to 192.168.255.255, 172.16.. to 172.16.255.255, 10… to ten.255.255.255. Functioning with your network administrator(s), we help analyze … Continue reading >>>
The Part Of Details Technologies In Company Success
 No longer a dream or rumor—predictable pc charges and trustworthy company technology is just a phone get in touch with away. Info that ordinarily would have taken scores of days and weeks to transport can now be gotten in a matter of seconds. Session 12 of this course will furnish you with detailed facts about the World wide web and E-commerce. This discuss will for that reason not only examine the Influence ICT has made so far on Human Socio-economic development but also proffer how it could further be enhanced and embraced in bringing about greater development. Considerably has been said on the topic of information and communication technologies effect on human socio-economic development.
No longer a dream or rumor—predictable pc charges and trustworthy company technology is just a phone get in touch with away. Info that ordinarily would have taken scores of days and weeks to transport can now be gotten in a matter of seconds. Session 12 of this course will furnish you with detailed facts about the World wide web and E-commerce. This discuss will for that reason not only examine the Influence ICT has made so far on Human Socio-economic development but also proffer how it could further be enhanced and embraced in bringing about greater development. Considerably has been said on the topic of information and communication technologies effect on human socio-economic development.
At McCann, you will have access to pc labs where you can do homework and verify your email in among classes. Then think about enrolling in the Data Processing system at McCann School of Business & … Continue reading >>>
What Is A Campus Region Network (CAN)?
 A campus network is a constructing or group of buildings all connected into one enterprise network that consists of lots of regional-location networks (LANs). Chapters 10, 11, 12 and 13, respectively deliver the capabilities required for troubleshooting and analyzing Campus IPX Networks, AppleTalk Networks, Windows Networking and Wide Region Networks. Campus networks usually use LAN technologies, such as Ethernet, Token Ring, Fiber Distributed Information Interface (FDDI), Quick Ethernet, Gigabit Ethernet, and Asynchronous Transfer Mode (ATM). The information are explained quite well and will assist me pass the Cisco Help test. Of course, if you want to hold your troubleshooting tasks to a minimum, then get her style book as properly.
A campus network is a constructing or group of buildings all connected into one enterprise network that consists of lots of regional-location networks (LANs). Chapters 10, 11, 12 and 13, respectively deliver the capabilities required for troubleshooting and analyzing Campus IPX Networks, AppleTalk Networks, Windows Networking and Wide Region Networks. Campus networks usually use LAN technologies, such as Ethernet, Token Ring, Fiber Distributed Information Interface (FDDI), Quick Ethernet, Gigabit Ethernet, and Asynchronous Transfer Mode (ATM). The information are explained quite well and will assist me pass the Cisco Help test. Of course, if you want to hold your troubleshooting tasks to a minimum, then get her style book as properly.
When connecting a Cisco IOS software device to a CatOS device, make sure that PAgP settings are the very same on both sides. In basic practice, the most deterministic and ideal-performing networks in terms of convergence, reliability, and manageability are … Continue reading >>>
Computer Security And Forensics
 In addition to these cutting edge subjects, you will also find out how to create systems, procedures, and human resources to manage the risks related with data technologies – and be capable of supplying technical help to stop, investigate, and defend folks and organizations from cyber-crime. An individual’s personal personal computer is threatened just as a lot as large servers and networks operated by organizations and as a consequence, interest in computer security is higher. Public Security and Security — Expertise of relevant equipment, policies, procedures, and strategies to promote efficient local, state, or national security operations for the protection of people, information, home, and institutions.
In addition to these cutting edge subjects, you will also find out how to create systems, procedures, and human resources to manage the risks related with data technologies – and be capable of supplying technical help to stop, investigate, and defend folks and organizations from cyber-crime. An individual’s personal personal computer is threatened just as a lot as large servers and networks operated by organizations and as a consequence, interest in computer security is higher. Public Security and Security — Expertise of relevant equipment, policies, procedures, and strategies to promote efficient local, state, or national security operations for the protection of people, information, home, and institutions.
Buyer and Private Service — Understanding of principles and processes for supplying customer and personal solutions. Your research will also cover effective computer system systems management and how to comprehensive an productive IT wellness check. Working Circumstances — Occupations that satisfy this perform value … Continue reading >>>







