Banking In India
 Fiberbit Self Study Weblog, Shortening Your Finding out Curve Frequent articles for fiber networks, Networking and Technology. Packet switching may perhaps be employed internally by backbone networks to take benefit of these visitors patterns, even though the backbone network may well present a circuit-switching appearance to external hosts (see virtual circuit ). Targeted traffic-pattern analysis may be made use of to construct backbone networks that decrease particular network parameters, such as typical delay, circuit expenses, etc.
Fiberbit Self Study Weblog, Shortening Your Finding out Curve Frequent articles for fiber networks, Networking and Technology. Packet switching may perhaps be employed internally by backbone networks to take benefit of these visitors patterns, even though the backbone network may well present a circuit-switching appearance to external hosts (see virtual circuit ). Targeted traffic-pattern analysis may be made use of to construct backbone networks that decrease particular network parameters, such as typical delay, circuit expenses, etc.
Switched Token Ring is comparable to switched ethernet,in that a token ring switch replaces the token ring hub, providing a series of point-to-point connections from the computers to the switch rather of the traditional shared circuit. A single of the most prevalent makes use of of gateways is to enable LANs that use TCP/IP and ethernet to communicate with IBM mainframes that use SNA. Sales of token ring have declined in current years as … Continue reading >>>

 The field of computer forensics is rapidly expanding and our specialist Personal computer Forensics degree – the very first in London – develops the robust logical expertise necessary to detect, investigate and avert laptop crime. Other job titles inside the field of computer forensics incorporate information and facts security specialist, global safety investigator, information and facts security forensics Consultant, forensic technologist, digital forensics specialist, vulnerability security study engineer, cyber terrorism liaison officer and much more. Purdue University in Indiana has a master of science (MS) in laptop and data technology with a specialization in cyberforensics. St. Petersburg College of Florida provides an on-line associate of science (AS) in digital forensics and computer investigations.
The field of computer forensics is rapidly expanding and our specialist Personal computer Forensics degree – the very first in London – develops the robust logical expertise necessary to detect, investigate and avert laptop crime. Other job titles inside the field of computer forensics incorporate information and facts security specialist, global safety investigator, information and facts security forensics Consultant, forensic technologist, digital forensics specialist, vulnerability security study engineer, cyber terrorism liaison officer and much more. Purdue University in Indiana has a master of science (MS) in laptop and data technology with a specialization in cyberforensics. St. Petersburg College of Florida provides an on-line associate of science (AS) in digital forensics and computer investigations.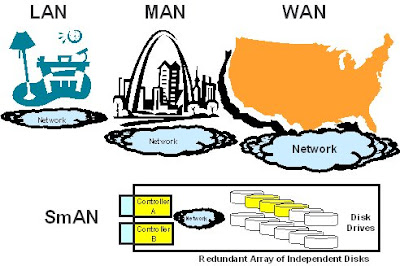 Clipping is a handy way to gather and organize the most essential slides from a presentation. This is a network that connects two or far more LANs but that is restricted to a particular and contiguous geographical region such as a college campus, industrial complex, workplace building, or a military base. MANs can bridge Local Location Networks without having any cables by making use of microwave, radio wireless communication or infra-red laser which transmits information wirelessly.
Clipping is a handy way to gather and organize the most essential slides from a presentation. This is a network that connects two or far more LANs but that is restricted to a particular and contiguous geographical region such as a college campus, industrial complex, workplace building, or a military base. MANs can bridge Local Location Networks without having any cables by making use of microwave, radio wireless communication or infra-red laser which transmits information wirelessly. The Laptop-Aided Design and style (CAD) program is made to give students entry-level style expertise in five locations. CAD software for mechanical design uses either vector-primarily based graphics to depict the objects of conventional drafting, or could also produce raster graphics showing the overall look of made objects. In recent years, the School of Computing, Engineering and Physical Sciences has moved into a brand new constructing with impressive laptop facilities and specialist labs.
The Laptop-Aided Design and style (CAD) program is made to give students entry-level style expertise in five locations. CAD software for mechanical design uses either vector-primarily based graphics to depict the objects of conventional drafting, or could also produce raster graphics showing the overall look of made objects. In recent years, the School of Computing, Engineering and Physical Sciences has moved into a brand new constructing with impressive laptop facilities and specialist labs. Connected tasks contain testing , debugging , and maintaining the supply code , implementation of the build technique, and management of derived artifacts such as machine code of computer programs These could be thought of element of the programming course of action, but often the term computer software development is made use of for this larger approach with the term programming, implementation, or coding reserved for the actual writing of supply code. Some students take jobs in the technologies field right after earning their associate degree others use it as a springboard for a four-year system. Computer programming relies on logic, so students will be expected to develop each their math and trouble-solving capabilities in concert. They routinely test code by looking for errors — sections of code that the computer system does not have an understanding of — and debugging applications.
Connected tasks contain testing , debugging , and maintaining the supply code , implementation of the build technique, and management of derived artifacts such as machine code of computer programs These could be thought of element of the programming course of action, but often the term computer software development is made use of for this larger approach with the term programming, implementation, or coding reserved for the actual writing of supply code. Some students take jobs in the technologies field right after earning their associate degree others use it as a springboard for a four-year system. Computer programming relies on logic, so students will be expected to develop each their math and trouble-solving capabilities in concert. They routinely test code by looking for errors — sections of code that the computer system does not have an understanding of — and debugging applications.





